Products
SAC Solutions products are tailored and created specifically
to operate and maintain cyber security in ICS / IACS / OT Environments.
FacOTry 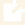
Our FacOTry product offers a non-invasive, efficient, and seamlessly integrated solution for managing and operating cyber security in your OT infrastructure.
FacOTry provides a coherent approach to safeguarding your critical assets.
Network visibility
Gain enhanced visibility into your OT network with our Network visibility product. Our intrusion detection product is configures and optimized to provided real-time detection and alerts for any know bad OT cyber security attacks.
Stay one step ahead of threats to protect your critical infrastructure.
Security baseline
Our security baseline product helps you establish a realistic OT security roadmap that aligns with your capabilities, resources, compliance requirements, and overall strategy.
It enables you to develop a solid foundation for effectively protecting your OT infrastructure.
Site assessment
There are 5 types of appraisals/assessment of OT security:
-
-
- Site
- Baseline
- Employer requirements
- Risk
- GAP
-
FacOTry 
Network visibility
Security baseline
Site assessment
Network visibility
security and resilience of the control networks
WHY IS NETWORK VISIBILITY IMPORTANT
Network visibility together with control and monitoring at primary zones boundaries, is of significant importance in ICS (Industrial Control Systems) OT environments, particularly when it comes to the connection between the DMZ (Demilitarized Zone) and control systems, as well as third-party vendor systems within the control networks.
Network visibility plays a critical role in ICS OT environments, particularly when considering:
- the connection between the DMZ,
- access from DMZ to control systems,
- remote machine or human third-party vendor access to your infrastructure.
It enables security monitoring, intrusion detection, incident response, vendor system monitoring, compliance, network performance optimization, and overall enhances the security and resilience of the control networks.

Incident Response and Forensics
Network visibility provides crucial data for incident response and forensic investigations in the event of a security breach or incident. By capturing and analysing network traffic logs, organisations can reconstruct events, determine the scope and impact of the incident, and identify the root causes. This information is essential for remediation, recovery, and strengthening security measures to prevent similar incidents in the future.
Security Monitoring
Network visibility allows for comprehensive security monitoring and threat detection. By monitoring network traffic and analysing network data, security teams can identify potential security incidents, anomalies, or suspicious activities in real-time. This enables early detection and prompt response to mitigate risks and prevent cyber threats from propagating within the control systems.
Vendor System Monitoring
In ICS OT (Industrial Control System Operational Technology) environments, third-party vendors often have access to control systems for maintenance, support, or system integration purposes. Network visibility allows you to monitor the activities of these vendor systems within the control networks. It helps ensure that vendor systems are properly authorised, adhere to security policies and practices, and do not introduce any vulnerabilities or unauthorised changes that could compromise the integrity or availability of the control systems.
Compliance and Auditing
Network visibility facilitates compliance with regulatory requirements and industry standards in ICS OT environments. It allows you to monitor and track network activity to demonstrate adherence to security policies, access controls, and data protection measures. Network visibility also enables you to generate audit logs and reports for regulatory compliance audits, internal assessments, and management reviews.
Intrusion Detection and Prevention
With network visibility, you can implement Intrusion Detection Systems and Intrusion Prevention Systems (IDS/IPS) to monitor the network for unauthorised access attempts, malware infections, or other malicious activities. IDS/IPS solutions can analyse network traffic patterns, signatures, and behaviours to identify potential intrusions and take proactive measures to block or mitigate them. This helps protect the integrity and availability of critical control systems.
Network Performance and Optimization
Network visibility provides insights into the performance and utilisation of network resources in ICS OT environments. By monitoring network traffic and analysing data, organisations can identify bottlenecks, optimise network configurations, and ensure efficient data transfer between the DMZ, control systems, and third-party vendor systems. This helps maintain smooth operations, minimise latency, and ensure reliable communication between critical components.
Security baseline
for a secure and resilient OT environment
Why do security baselining?
In the field of OT (Operational Technology) cyber security, establishing a security baseline is crucial for maintaining a secure and resilient OT environment.
A security baseline refers to a set of standards, configurations, and practices that define the minimum level of security requirements for the OT systems and infrastructure.
A security baseline helps establish a solid foundation for security and serves as a reference point for assessing and improving the security posture of the OT environment.
SAC Solutions provided a range of ICS OT security products and services enhancing your security: UniversiOTy, FacOTry, MoniOTr & SecureScope.
These products all hugly profit of creation of a security baseline. In the context of security baselining, these products can be integrated as strong supplementary components.
Overall, the combination of these products can support organizations in establishing and maintaining a secure and resilient OT environment by providing education, tools, and ongoing defense capabilities.
UniversiOTy SAC Solutions can provide the necessary education and training to understand the concepts and best practices related to security baselining.
FacOTry can be utilized as a tool to implement and enforce the security baseline by offering guidelines, methodologies, and simplified tooling.
MoniOTr can complement the security baseline by providing ongoing monitoring, management, and response capabilities to ensure the security of the OT infrastructure.
Why it is important
Consistency and Standardization
A security baseline ensures that all OT systems and components adhere to a consistent set of security configurations and practices. This helps reduce variations and inconsistencies in security measures, making it easier to manage and maintain a secure environment.
Risk Reduction
By defining a security baseline that includes essential security controls, organizations can mitigate common vulnerabilities and reduce the risk of successful cyber attacks or disruptions to their OT operations. It serves as a starting point for implementing security measures specific to the OT environment.
Incident Response and Recovery
Having a security baseline facilitates incident response and recovery efforts. By understanding the baseline configurations and security measures, organizations can quickly identify deviations and anomalies during an incident, enabling a faster response and restoration of services.
Compliance and Regulatory
Requirements Many industries and sectors have specific regulatory or compliance requirements for securing OT systems. A security baseline helps organizations align with these requirements and demonstrate compliance by implementing the necessary security controls and practices.
Activities in establishing a security baseline
Asset Identification
Identifying and inventorying all OT assets, including devices, systems, and network components, is crucial to understand the scope of the environment and determine which assets are included in the security baseline.
Risk Assessment
Conducting a comprehensive risk assessment helps identify potential threats and vulnerabilities within the OT environment. The results of the assessment inform the security controls and configurations included in the security baseline.
Security Control Selection and Configuration
Selecting appropriate security controls and configuring them according to best practices and industry standards are essential steps. These controls may include access controls, authentication mechanisms, encryption protocols, network segmentation, monitoring solutions, and more.
Documentation
Creating detailed documentation of the security baseline is important. This includes documenting the chosen security controls, their configurations, and any associated policies or procedures. The documentation serves as a reference for maintaining, updating, and auditing the security baseline.
The benefits
Security Baseline Document
This document outlines the specific security controls, configurations, and practices that form the baseline for the OT environment. It serves as a reference for implementing and maintaining security measures.
Configuration Standards
These are predefined and documented configurations for various OT components, such as network devices, controllers, and software applications. They define the recommended settings to achieve the desired security posture.
Monitoring and Auditing
Mechanisms Establishing monitoring and auditing mechanisms ensures ongoing compliance with the security baseline. These mechanisms help detect and respond to any deviations from the baseline and provide visibility into the security status of the OT environment.
Configuration Standards
These are predefined and documented configurations for various OT components, such as network devices, controllers, and software applications. They define the recommended settings to achieve the desired security posture.
Relation and coherence of ICS OT cyber security Closely related topics:
These cyber security activities are interconnected and contribute to a comprehensive approach in securing operational technology environments.
Overall, Vulnerability assessments, risk assessments, penetration testing, red teaming, ethical hacking, and security baselining are interconnected activities that support each other in strengthening the security of operational technology environments. They collectively contribute to identifying vulnerabilities, quantifying risks, testing defenses, and establishing a minimum security standard to mitigate potential threats and protect critical assets.
This is their relation and coherence to Security baseline:
Vulnerability Assessment
A vulnerability assessment is the process of identifying and quantifying vulnerabilities in a system or network. It involves scanning the infrastructure for known vulnerabilities and weaknesses, assessing their severity, and providing recommendations for mitigation. Vulnerability assessments provide valuable insights into potential security weaknesses that could be exploited by attackers.
Risk Assessment
Risk assessment involves evaluating the likelihood and potential impact of security risks on an organization’s assets and operations. It considers various factors, such as threats, vulnerabilities, and the value of assets, to prioritize and manage risks effectively. Risk assessment helps organizations understand the potential consequences of vulnerabilities identified in the vulnerability assessment and supports decision-making regarding risk mitigation strategies.
Penetration Testing
Penetration testing, also known as ethical hacking, involves actively testing the security of a system by simulating real-world attacks. It aims to identify vulnerabilities and weaknesses that may not be detected through automated scans or assessments. Penetration testing typically involves a systematic and controlled approach to exploit vulnerabilities, gain unauthorized access, and provide actionable recommendations for remediation.
Red Teaming
Red Teaming takes penetration testing to a broader and more comprehensive level. It involves a team of skilled professionals simulating realistic attack scenarios to assess an organization’s overall security posture. Red teaming goes beyond technical vulnerabilities and incorporates social engineering, physical security, and other factors to evaluate the effectiveness of an organization’s defenses. The goal is to identify and address potential security gaps from a holistic perspective.
Ethical Hacking
Ethical hacking refers to authorized activities performed by cybersecurity professionals to identify and address vulnerabilities in systems or networks. It involves using the same techniques and methodologies as malicious hackers but with the explicit purpose of improving security. Ethical hacking can encompass vulnerability assessments, penetration testing, and red teaming, depending on the scope and objectives of the engagement.
Security Baseline
A security baseline is a set of standards, configurations, and practices that define the minimum level of security requirements for an organization’s systems and infrastructure. It serves as a reference point for assessing and improving the security posture. A security baseline incorporates the results of vulnerability assessments, risk assessments, penetration testing, and red teaming exercises to establish a solid foundation for security measures.
Site assessment
Improved security as a result
WHAT & WHY
We will provide you with a site assessment. We will give you a bonus of a roadmap on how to move forward using the findings of the Site assessment along with the possibility of buying our Tool “FacOTry” that is specifically made to reduce the cost, resources needed (time, workers) and complexity of OT security.
We support you in solving tangible real-life problems.
OVERVIEW SITE ASSESSMENT
The assessement is not meant to be exhaustive, as such assessment would be an excessive use of resources, that would take away from resources needed afterwards to improve on the points found in the assessment report.
Our goal is to support you to become more secure, and for that goal, we do not want to needlessly take away from the time for improvements.
We will ONLY perform site assessments where on site assessment are allowed. We will NOT do an online review of the site as our experience is that many unexpected things are discovered in the on site inspection.
EXAMPLE OF ROADMAP
There are 5 types of assessment of OT security: Site, baseline, employer requeriments, risk, and GAP.
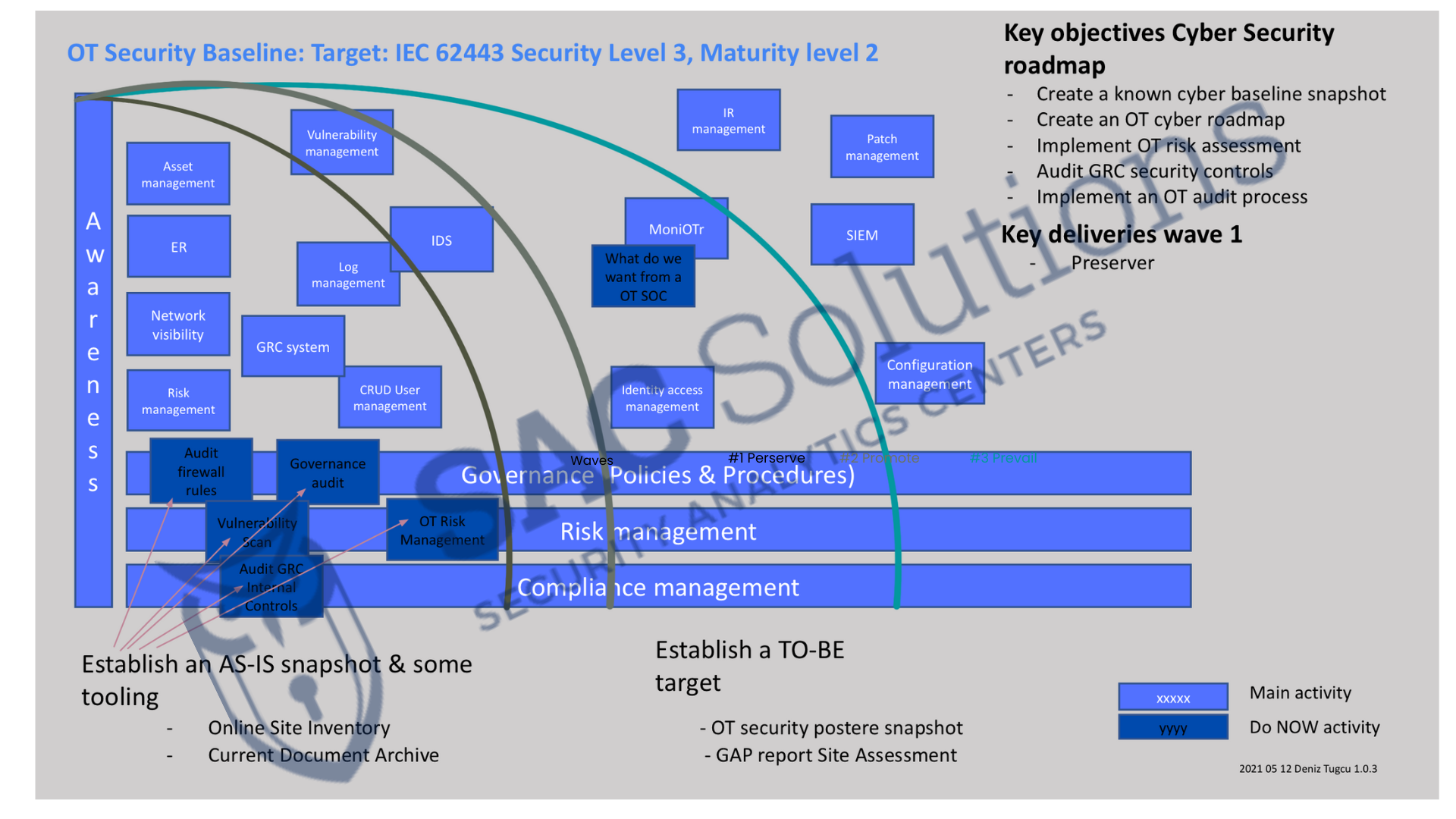
The PROCESS
PACKAGE OPTIONS
FacOTry Options – a promised part of our site assessment to ensure improved security as a result
Depending on what you choose and how long you need the site assessment and following security improvements to be we provide different options.
Note that with all of them, you get a full site assessment (preparation, on-site assessment, analysis, and a report), but the tools and further support in improvements afterward may vary.
The level of depth of the investigation along with the training may also vary depending on the client and we will help guide them on what we think is best for the given site and client.
The site report
Among other things we provide visualization and quick overview that includes evaluation of:
Includes proposal for: SL, ML and Functional requirements (based on IEC 62443-3-3)
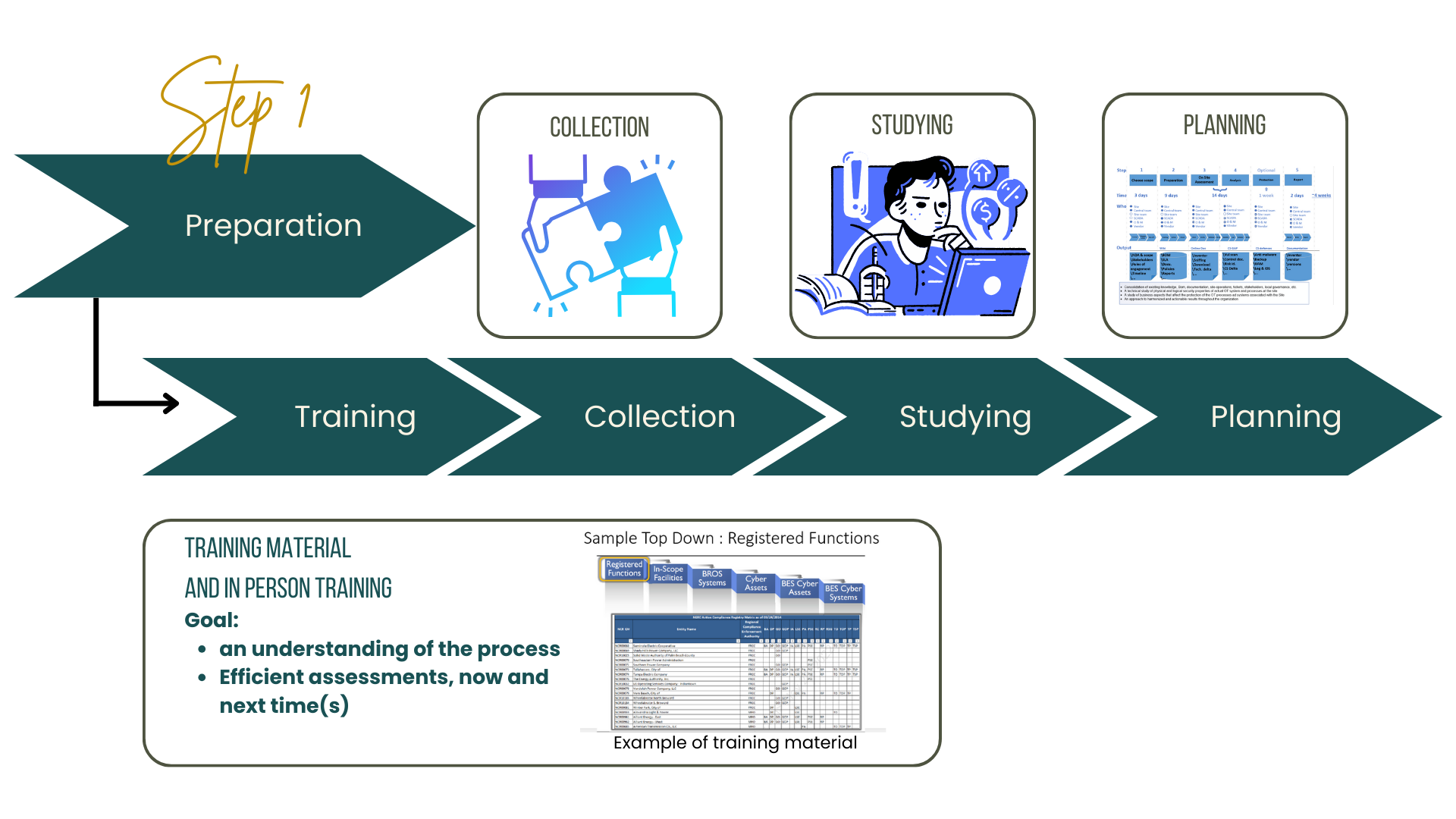
Preparation
The first step in site assessment is preparation.
Training equipment includes:
- PDF of a procedure document for site assessment.
- 3 hours presentation of the information, including the procedure and theories behind it.
Collection
A collection of existing information, provided by you (the company). The intention is to gather as much information about the site, operations, and security controls, to reduce the time needed for the site assessment.
Studying
Study the provided information to learn as much as possible about the target system from a lifecycle perspective.
Planning
The benefits of an exhaustive site assessment are diminishing after a certain level of investigation, prioritizing and planning based on the collected material, studying it along with strong teamwork between your specialist and our assessment team.
BONUS
Intro bonus from us
– Roadmap (free, goodwill)
– FacOTry (Free, data collection)
– Support (roadmap, FacOTry) if wanted (buy)
Preparation
The first step in site assessment is preparation.
Training equipment includes:
- PDF of a procedure document for site assessment.
- 3 hours presentation of the information, including the procedure and theories behind it.

Collection
A collection of existing information, provided by you (the company). The intention is to gather as much information about the site, operations, and security controls, to reduce the time needed for the site assessment.

Studying
Study the provided information to learn as much as possible about the target system from a lifecycle perspective.

Planning
The benefits of an exhaustive site assessment are diminishing after a certain level of investigation, prioritizing and planning based on the collected material, studying it along with strong teamwork between your specialist and our assessment team.
BONUS
Intro bonus from us
– Roadmap (free, goodwill)
– FacOTry (Free, data collection)
– Support (roadmap, FacOTry) if wanted (buy)